As a cybersecurity expert with two decades of experience, I’ve witnessed a wide spectrum of cyber threats. The threat landscape is constantly changing, but the underlying tactics and techniques used by cybercriminals often remain the same. In a recent incident, a small company I was consulting for was targeted by a spear-phishing campaign.
Despite having basic security protocols in place, one click on a malicious link, and the network was compromised, causing a data breach and extensive downtime. This highlighted that all companies, regardless of size, are vulnerable to a variety of cyber threats.
This article breaks down the top ten types of information security threats that IT teams should be vigilant about, with insights into how they work and how to guard against them.
1. Phishing Attacks

One of the most widespread types of cybersecurity threats, phishing attacks often begin with an innocent-looking email.
- They can target usernames, passwords, credit card numbers, and other personal information.
- Cybercriminals also use phishing attacks to distribute malware and ransomware.
The information acquired through phishing attacks is then used for malicious activities, including identity theft, financial fraud, or unauthorized access to systems.
How to Prevent Phishing Attacks
Phishing attacks can be difficult to prevent because they rely heavily on human interaction and trickery. However, there are steps that organizations can take to protect themselves:
- IT teams should implement email security systems that detect and block phishing attempts.
- Companies should regularly educate their employees about the risks of phishing and the signs to watch out for, including suspicious email addresses, spelling mistakes, and unexpected requests for personal information.
2. Ransomware Attacks
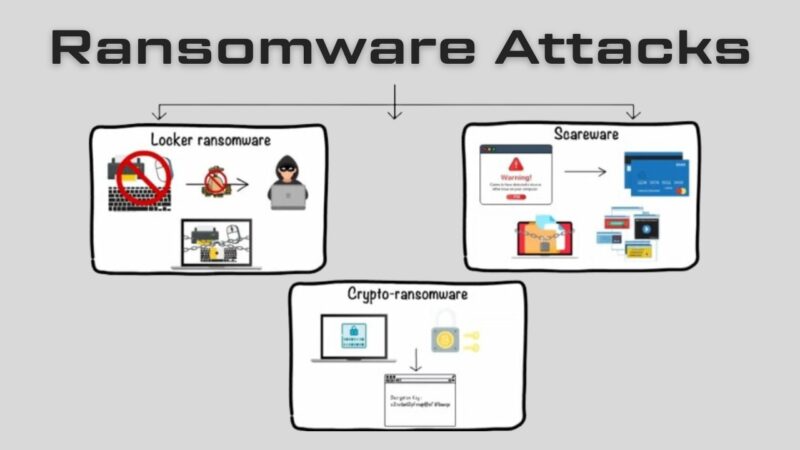
Ransomware attacks, where hackers hold data hostage for a ransom, have been in the spotlight in recent years due to their increased frequency and the extensive damage they cause.
Ransomware is a type of malware that encrypts an organization’s files or blocks access to their systems until a ransom is paid.
- The ransom is typically demanded in Bitcoin, making it nearly impossible to trace.
- These attacks can be incredibly damaging, leading to significant financial losses, downtime, and reputational harm.
Protecting Against Ransomware Attacks
To protect against ransomware attacks, organizations must adopt a multi-faceted approach:
- Regularly back up all important data and test backups to ensure they can be restored.
- Implement robust security solutions, including antivirus software, firewalls, and intrusion detection systems.
- Educate employees about the dangers of opening suspicious emails or clicking on unverified links.
3. Insider Threats
Insider threats, whether malicious or unintentional, pose a unique challenge because they come from within the organization.
These threats stem from employees, contractors, or business associates who have legitimate access to the company’s network, databases, and applications.
- Malicious insiders intentionally misuse their access to steal information, sabotage systems, or commit fraud.
- Unintentional insider threats arise when well-meaning employees accidentally expose sensitive information or fall victim to social engineering tactics.
Mitigating Insider Threats
Mitigating insider threats requires a balanced approach that combines technological solutions with a strong emphasis on employee education and a culture of security.
- Implement strict access control measures, ensuring that employees have access only to the information necessary for their jobs.
- Conduct regular security awareness training to inform employees about safe online behaviors.
4. DDoS Attacks
Distributed Denial of Service (DDoS) attacks can cripple an organization’s online presence and disrupt its operations.
Defining DDoS Attacks
In a DDoS attack, a multitude of compromised devices, often part of a botnet, are used to flood a target’s network or servers with traffic, causing them to slow down or crash.
- The intention isn’t to gain unauthorized access or steal data but to disrupt the target’s services, leading to financial loss and a damaged reputation.
Countering DDoS Attacks
Countering DDoS attacks demands a robust strategy that combines various layers of protection:
- Employ DDoS mitigation services that can identify and reroute malicious traffic.
- Regularly update and patch all devices to prevent them from being co-opted into a botnet.
5. Malware
Malware remains a persistent threat, with new variants constantly emerging.
Breaking Down Malware Threats
Malware is an umbrella term for various forms of malicious software, including viruses, worms, Trojans, spyware, and ransomware.
- These threats can damage systems, steal data, and create backdoors for future attacks.
Shielding from Malware
The fight against malware requires proactive and reactive measures:
- Use up-to-date antivirus software and regularly scan systems for threats.
- Enforce a strong patch management policy to close potential vulnerabilities that malware can exploit.
6. SQL Injection
SQL Injection attacks are a serious threat to any organization with a web presence.
It involves inserting malicious SQL code into a query to manipulate a web application’s database.
- Attackers can use this method to view, modify, or delete data.
Avoiding SQL Injection Attacks
There are a few key steps to take in order to avoid falling victim to SQL Injection attacks:
- Utilize parameterized queries or prepared statements to separate SQL code and data.
- Regularly update and patch web applications to close any existing vulnerabilities.
7. Password Attacks
Despite advancements in security technology, password attacks remain a common method used by cybercriminals.
Delving into Password Attacks
Password attacks involve attempting to gain unauthorized access to systems by cracking user passwords.
- Techniques include brute force, dictionary attacks, and keylogging.
Fending off Password Attacks
To fend off password attacks, organizations need to enforce stringent password policies:
- Use strong, complex passwords and change them regularly.
- Implement multi-factor authentication to add an extra layer of security.
8. Man-In-The-Middle Attacks
Man-in-the-middle (MitM) attacks are a serious concern, particularly for organizations that heavily rely on online transactions.
In a MitM attack, the hacker positions themselves between the communication of two parties.
- This allows them to eavesdrop, manipulate the conversation, or steal sensitive data.
Stopping MitM Attacks
Preventing MitM attacks involves securing communication channels and authenticating users:
- Use encryption protocols like HTTPS for all online communications.
- Employ secure email gateways to filter out potential phishing or spoofing attempts.
9. Advanced Persistent Threats
Advanced Persistent Threats (APTs) represent the pinnacle of cyber warfare, often attributed to state-sponsored actors.
APTs are long-term, targeted attacks where the intruder gains access to a network and remains undetected for an extended period.
- During this time, they steal data, monitor activities, and create additional points of entry.
Warding off APTs
APTs require a layered defense strategy due to their complexity:
- Use threat intelligence to understand and anticipate potential threats.
- Regularly audit and monitor network activities to spot any unusual behavior.
10. Zero-Day Attacks
Zero-Day attacks exploit unknown vulnerabilities, making them particularly hard to guard against.
This attack occurs when a hacker exploits a software vulnerability before the vendor has had a chance to create a patch.
- This leaves the software’s users vulnerable to an attack.
Combating Zero-Day Attacks
Dealing with Zero-Day attacks requires proactive security measures:
- Employ security solutions that use behavioral analysis to detect unusual activity, which may indicate a Zero-Day attack.
- Participate in a bug bounty program to incentivize the discovery and reporting of vulnerabilities.
FAQs

What Is an Insider Threat?
An insider threat occurs when individuals close to an organization who has authorized access to its network intentionally or unintentionally misuse that access to negatively affect the organization’s critical data or systems.
This can be due to careless employees who don’t comply with their organizations’ business rules and policies or malicious insiders intentionally bypassing security measures to delete data, steal data, disrupt operations, or otherwise harm the business.
What Are Viruses and Worms?
Viruses and worms are malicious software programs (malware) aimed at destroying an organization’s systems, data, and network. A computer virus is a malicious code that replicates by copying itself to another program, system, or host file.
A computer worm is a self-replicating program that doesn’t have to copy itself to a host program or require human interaction to spread.
What Is a Botnet?
A botnet is a collection of Internet-connected devices, including PCs, mobile devices, servers, and IoT devices, that are infected and remotely controlled by a common type of malware.
The goal of the threat actor creating a botnet is to infect as many connected devices as possible, using the computing power and resources of those devices for automated tasks that generally remain hidden from the users of the devices.
What Is a Drive-By Download Attack?
In a drive-by download attack, malicious code is downloaded from a website via a browser, application, or integrated operating system without a user’s permission or knowledge. A user doesn’t have to click on anything to activate the download. Just accessing or browsing a website can start a download.
What Are Exploit Kits?
An exploit kit is a programming tool that enables a person without any experience writing software code to create, customize, and distribute malware. Cybercriminals use these toolkits to attack system vulnerabilities to distribute malware or engage in other malicious activities.
What Is Malvertising?
Malvertising is a technique cybercriminals use to inject malicious code into legitimate online advertising networks and web pages. This code typically redirects users to malicious websites or installs malware on their computers or mobile devices.
Final Words
The world of cybersecurity is continually evolving, and so too, are the threats that organizations face. By understanding the top threats, IT teams can better defend their networks and systems, ensuring the safety of their data and the continuity of their operations.
With diligent preparation, the right tools, and a culture of security awareness, organizations can stay one step ahead of the threats.
For a comprehensive understanding of safeguarding sensitive data and maintaining online safety, it’s essential to be familiar with the fundamental guidelines outlined in the article “Principles of Information Security.”
You can create a presentation on these security threat for your IT team with Adobe’s free slide deck background templates.

